Cyber Security Penetration testing
We recognize the critical importance of robust cyber security in today's digital landscape. As businesses
increasingly rely on technology to drive their operations, the need for a secure and resilient IT
infrastructure has never been more vital. Our Penetration Testing services are a cornerstone in fortifying
your digital defenses, offering a comprehensive and proactive approach to identifying and addressing
vulnerabilities.
Understanding penetration testing
Penetration Testing, also known as ethical hacking, simulates real-world cyber-attacks to evaluate the
security posture of your systems, networks, and applications. RND Softech employs a team of seasoned
cybersecurity experts who leverage industry-leading methodologies and cutting-edge tools to mimic
malicious actors' tactics, techniques, and procedures. Our goal is to uncover vulnerabilities before
cybercriminals can exploit them.


 Campaigns.webp)


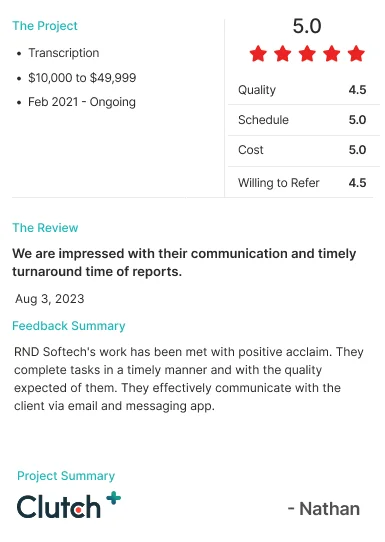
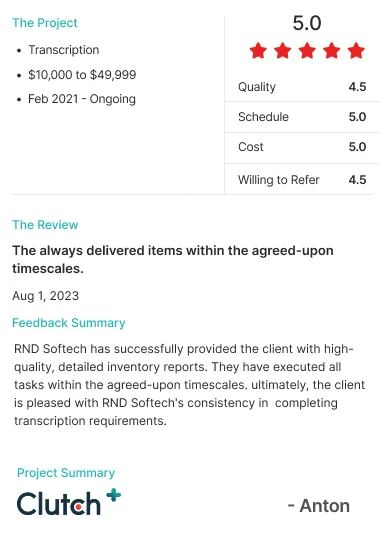
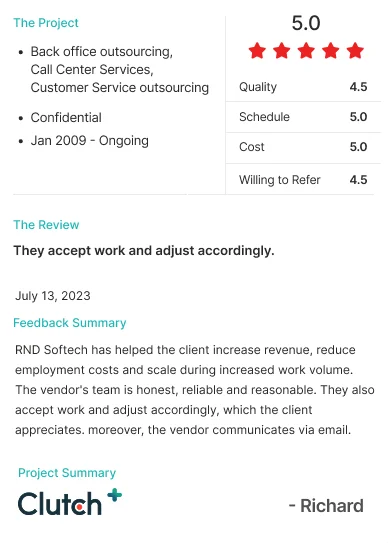







.webp)