In choosing our Risk Assessment needs, you not only gain access to cutting-edge services but also unlock a spectrum of benefits that propel your business towards a resilient and secure future. Our commitment is ingrained in proactively identifying, addressing, and mitigating risks, Enabling you to concentrate on your primary business activities with confidence.
Risk assessment
We specialize in offering comprehensive Risk Assessment services Customized to fulfill the distinct requirements of our clientele. Our expert team excels in navigating the intricate landscape of potential risks, ensuring a secure and resilient foundation for your business.
Our services

Risk profiling
- Service Profiling potential risks specific to your industry and business. Benefiting Uncovering Hidden Threats and vulnerabilities, allowing for proactive risk management.

Threat identification
- Service Identifying and analyzing potential threats in real time. Benefiting Staying one step ahead, minimizing the impact of unforeseen challenges.
Vulnerability assessment
- Service Conducting thorough vulnerability reviews on your systems and processes. Benefiting strengthening your defences by addressing weaknesses and fortifying security measures.

Compliance evaluation
- Service Ensuring adherence to industry regulations and compliance standards. Benefiting Avoiding legal complications and fostering a culture of transparency and responsibility.

Cyber security audits
- Service Regular audits to evaluate and enhance cyber security measures. Benefiting Safeguarding digital assets, ensuring the preservation of data integrity and fostering trust among stakeholders.

Continuity planning
- Service Developing robust business continuity and disaster recovery plans. Benefiting ensuring uninterrupted operations during unforeseen events, minimizing downtime.

Training and awareness programs
- Service Conducting training sessions to enhance staff awareness of potential risks. Benefiting empowering your team to be the first line of defence against emerging threats.

Incident response services
- Service Rapid response and mitigation approaches in the case of a security breach. Benefiting, minimizing damage, restoring normalcy, and preventing future occurrences.

Data privacy assessment
- Service Evaluating and ensuring compliance with data protection and privacy laws. Benefiting Enhancing customer trust, avoiding legal penalties and securing sensitive information.

Customized risk mitigation strategies
- Service Tailoring risk mitigation plans based on your specific business requirements. Benefiting Implementing targeted solutions that align with your unique operational environment.
FREQUENTLY
Asked Questions
The business world is being flattered by economics,technology,demographics and regulations.To win in this
flattering world,companies must transform
their way of working to seek and convert new opportunities
wherever those opportunities may be.This means acquiring the ability to disaggregate your
operations,people and resources across time zones,geographies,cultures and sourcing and delivering.
What is a Risk Assessment?
A Risk Assessment identifies and analyzes potential risks to an organization, allowing for the prioritization of resources and strategies to mitigate these risks effectively.
What is Penetration Testing?
Penetration Testing involves simulating real cyberattacks on an organization's systems to uncover vulnerabilities and weaknesses before malicious actors can exploit them.
How does RND Softech conduct Vulnerability Management?
RND Softech identifies, assesses, and prioritizes vulnerabilities in your systems and software, followed by implementing necessary patches and safeguards to prevent security breaches.
What is Data Privacy and Protection?
Data Privacy and Protection involve implementing measures to secure sensitive data in compliance with data protection laws and regulations.
How does Business Continuity Planning work?
Business Continuity Planning involves developing strategies and processes to ensure essential business functions continue during disruptions such as emergencies or cyberattacks.
How does RND Softech customize solutions for individual organizations?
RND Softech's team of experts understands the unique needs of different industries and tailors solutions to match specific security and compliance requirements.
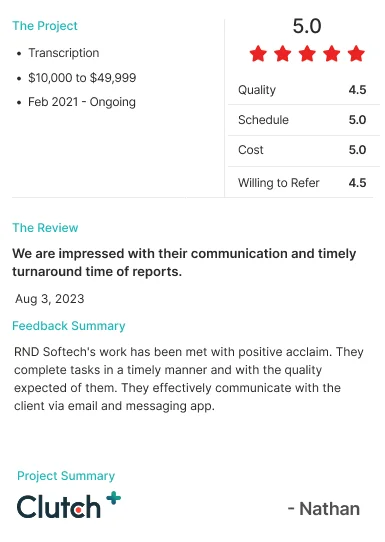
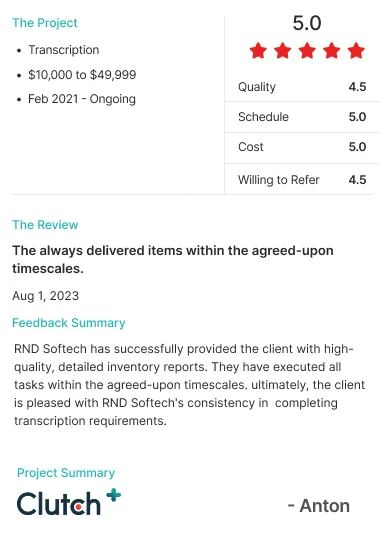
Our
TESTIMONIALS
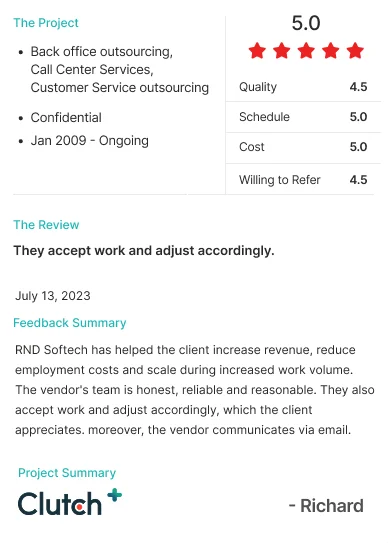
Our
CERTIFICATES
RND Softech, is a 25 year old Pioneer Off-shore BPO staffing partner servicing the US , UK, Canada & Australian markets across 15+ Back office support domains.
Contact
Have Project on your Mind? Drop your Details here
Use our contact form for all information request or contact us directly using the contact information below. All information is treated with complete confidentiality and in accordance with our data protection statement
+1 844 763 7638
+1 832 369 6801

INDIA
274/4, Anna Private Industrial Estate, Vilankuruchi Road, Coimbatore, Tamil Nadu 641035.
.webp)
USA
RND Softech INC,12909, Jess Pirtle Boulevard,Sugar Land, Texas 77478, United States
TALK TO OUR EXPERTS
Schedule your free consultation
More than 250+ clients worldwide work with us