Security configuration
Security has become a paramount concern for businesses worldwide in an era of digital advancements. At RND Softech, we understand the critical importance of fortifying your digital infrastructure against potential threats. Our comprehensive "Security Configuration." Services are meticulously crafted to protect your valuable assets' confidentiality, integrity, and availability.
Services offered
Network security configuration
- Our team of seasoned experts meticulously configures your network security parameters, including firewalls, intrusion detection/prevention systems, and VPNs. We tailor configurations to align with your business requirements, ensuring a seamless yet impervious digital environment.
Endpoint security configuration
- Protecting endpoints is crucial in the face of evolving cyber threats. Our specialists configure endpoint security solutions, such as antivirus software, endpoint detection and response (EDR) tools, and device control policies, creating a formidable defense against malicious entities.
Cloud security configuration
- Embrace the benefits of the cloud without compromising on security, RND Softech configures cloud security settings, encryption protocols, and access controls to safeguard your data and applications in cloud environments, ensuring a secure and compliant cloud infrastructure.
Application security configuration
- Applications are prime targets for cyber threats. Our experts focus on configuring application security settings, employing secure coding practices, and implementing web application firewalls to mitigate vulnerabilities and fortify your applications against potential exploits.
Identity and access management configuration
- Safeguarding user identities and controlling access is integral to security. We configure robust identity and access management solutions, implementing multi-factor authentication, role-based access controls, and identity federation to ensure that only authorized personnel access your critical systems and data.
Benefits of our choosing our security configurationing services
Holistic protection
Our services provide end-to-end security configurations, ensuring a comprehensive shield against diverse cyber threats. We address vulnerabilities across networks, endpoints, cloud environments, applications, and identity management systems.
Tailored solutions
Recognizing that each business has a unique security needs, we customize our configurations to align with your requirements. This ensures that the security measures are effective and efficient without unnecessary complexities.
Proactive threat mitigation
By configuring security settings with a proactive mindset, we anticipate potential threats and implement measures to mitigate them before they pose a risk to your organization. This approach enhances your overall security posture
Regulatory compliance
We ensure that our security configurations align with industry standards and regulatory requirements. This protects your organization from legal ramifications and instills trust in your stakeholders.
Continuous monitoring and updates
Security is an ongoing process. We provide continuous monitoring services and timely updates to adapt to emerging threats and maintain the resilience of your security infrastructure.
At RND Softech, our Security Configuration services are designed to empower your organization with confidence from a robust and adaptive security posture. Let us be your trusted partner in securing your digital assets against the ever-evolving landscape of cyber threats.






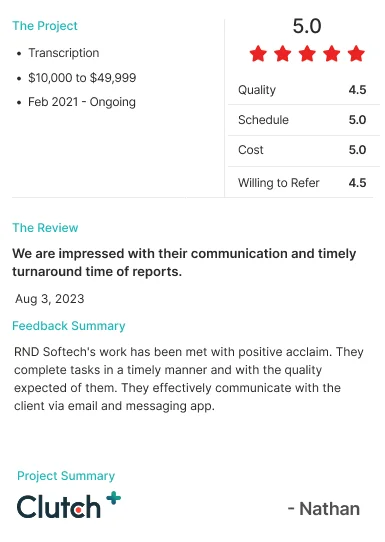
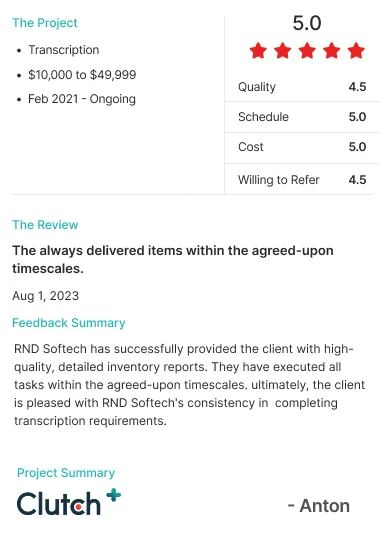
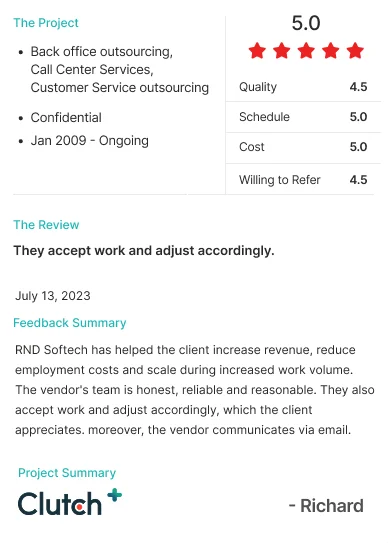







.webp)